现代化和数字化转型的好处是推动每个工业领域的企业转向新的网络物理系统技术,从而有可能以更高的效率和灵活性来收集和分析丰富的资产数据。但是,除了可以实现的生产力和安全性增长之外全面的工业网络安全保护also increases as the attack surface of the plant expands.
Leaning on our deep knowledge and global expertise in关键的基础设施保护,Nexus控制设计并部署整体操作技术(OT) cybersecurity solutionstailored to the unique demands of your industrial plant network.
Nexus Controls can ensure that you have aneffective cybersecurity programthat meets the needs oflegacy control systems, with limited expert resources, while accounting for modern technology andincreasing cyber threats.
By leveraging Nexus Controls' 60-year industrial domain expertise and tailoring industrial cybersecurity solutions specific to customer industrial control systems (ICS) use cases, you can be confident that Nexus OTArmor™ exceeds alternative ICS cybersecurity solutions on the market today.
一种创新的策略驱使我们。我们有一个完整的端到端网络安全投资组合。在悠久的历史中,我们专注于持续创新,并开发了我们的投资组合,包括旨在捍卫工业关键资产的广泛服务和解决方案。实际上,我们不提供的唯一控制是网络安全保险。但是除此之外,我们还为每种业务用例或挑战都有一些东西。
OurOTArmorCybersecurity Platform offers the following solutions for your organization's cybersecurity needs:
- Anti-virus
- 申请白列表
- Asset management
- Back-up and recovery
- Data diodes
- Intrusion detection/prevention systems (IDS/IPS)
- Multi-factor authentication (2FA)
- 下一代防火墙
- 补丁管理(集中式)
- Role-based access
- Security Information & Event Management (SIEM)
- Secure remote access
- Virtual private network (VPN)

重要的是要start withsome kind of benchmarkto understand the current state of security readiness. We provide a large variety of security assessment services. They are designed so the CEO, CISO, Plant Manager, or Compliance Manager to prioritize steps for mitigation, and even to help obtain future budgets within a multi-year cybersecurity program.
- 有助于获得预算和优先级网络安全路线图
- Understanding current state of security readiness
- Your results versus industry expectations
- Identify weakness early to prevent exploitation
- 提供优先的,可行的缓解步骤
Types of Assessments Offered:
- CIS Top 20 Controls
- Highly complex risk assessments or Penetration tests
- Product security assessment (IIOT, Controller, etc.)
- Compliance gap (NERC, NEI, IEC, etc.)
- Adversary Emulating Red Team Engagements
- Hunting as a Service (HaaS)
- Credential Risk Assessment

Managed Security Services
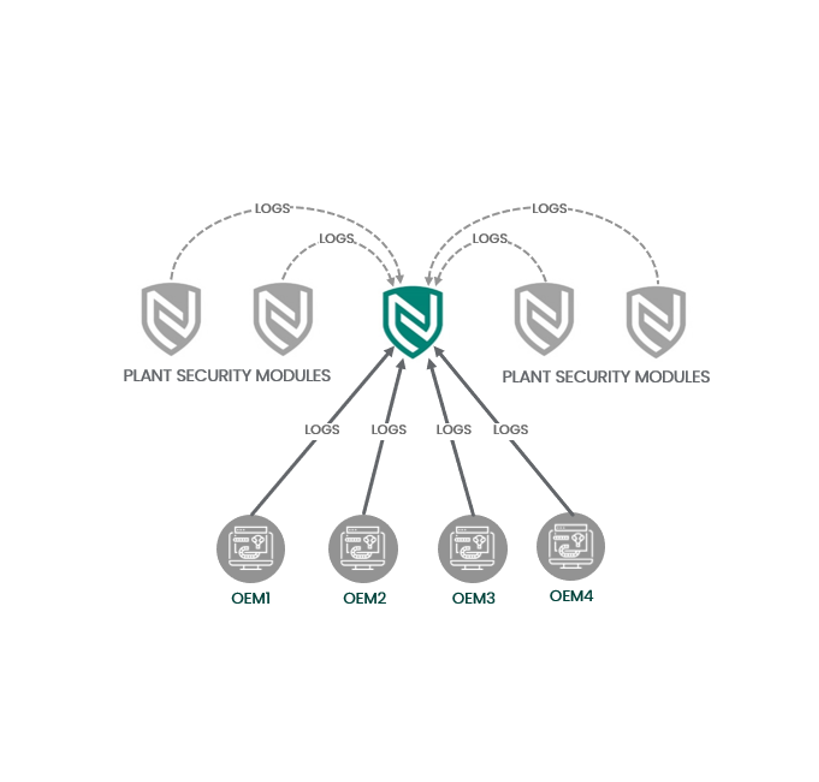
Nexus Controls’ team of cybersecurity analysts are expertsin big data solutions likeElastic Search, Splunk, and Hadoop. our highly skilled forensic analysts review relevant logs to minimize false positives and maximize the detection of threats. Whether you already have a Security Operations Center (SOC) or not, our 24X7 managed security services are scalable to meet your unique needs.
Patching Programs
Cyber Asset Protection (CAP)is a key part of a defense-in-depth system for turbine, plant, and generator controls environments. The patching program includes operating system and application patches as well as anti-virus/ intrusion detection signatures to cover updates for HMIs, servers, switches, and network intrusion detection devices. Monthly updates can be applied to individual HMIs or via the NexusOTArmor网络部署平台

IEC 62443-2-4(maturity level 2) certification ensures secure lifecycle of NexusOTArmoras an integrated system. This ensures safe industrial operations through a detailed analysis of our engineering processes throghout the security lifecycle; product design, manufacturing, network and system security, installation, and commisioning.
IEC 62443 3-3(security level 3) certified industrial cybersecurity platform that ensures that the NexusOTArmor网络安全solution was engineered utilizing a secure product development lifecycle process that includes IEC defined functionality and maintainable security. Additionally, this certification validates that the NexusOTArmor投资组合对安全风险进行了严格的测试。
These important industry certifications demonstrate our commitment to protecting industrial customers, including assisting them with regulatory and compliance requirements including NERC, NEI 08-9, CIS and NIST.
As a provider of comprehensive cybersecurity solutions across multiple industries, Nexus Controls is well-equipped to help your industrial plants achievesafety, zero unplanned downtime, 和operational efficiency:
操作员网络安全仪表板
- Nexus Controls designed dashboards
- Data-rich Security Incidents & Events Management (SIEM)
- 准备好安全内核ity Operator Center (SOC) integration
- Industrial process control experienced
- 摄入相关的日志以最大程度地减少误报以最大化检测和取证
- Expert system assists analysts for human evaluation of most important threats
- 24x7 operations, geographically distributed
- Full integration with holistic threat intelligence (not just another feed)
- Human-Led, OT/IT technology accelerated

现场安全评估:
- Optimize Production and System Reliability
- Identify, prioritize, and mitigate risks that impact critical production systems
- 调整网络体系结构和信息流以提高弹性和可靠性
- Improve Overall Security
- Evaluate people, architecture, and technology to identify weaknesses and mitigation strategies
- Address individual weaknesses in systems, assets, or data flow with comprehensive findings
- Enable Compliance Efforts
- 微调安全政策和实践,以符合相关的行业标准,法规和最佳实践
- Maintain comprehensive reports and documentation to assist with regulatory compliance efforts and audits for IEC62443, ISA99, and more
Product Development Security Assessments:
- Improve product security
- Address product weaknesses during development to reduce the risk of a public breach
- Reduce product costs
- Reduce the cost of remediation of security risks typically found after product deployment
- Enable compliance efforts
- Process improvement recommendations align with relevant industry standards, regulations, and best practices
- Gain a competitive advantage with customers who have supplier compliance requirements

资产识别
- 识别并列出监视网络上存在的资产
- Identify information such as make, model, firmware, Operating System, installed software
Asset Configuration Change Detection
- Identify if a change has occurred over the network or to the devices on the network which may indicate a compromise
- 确定工业设备是否发生了更改,这可能是妥协的指标
Methods of Discovery
- Active discovery
- Passive discovery
- Hybrid discovery
Detecting, Responding & Prevention
- Detecting cyber threats and possible breach activity
- Responding to deviations with high value/low volume alerts
- Prevention through adapting and prioritizing threats and change deviations
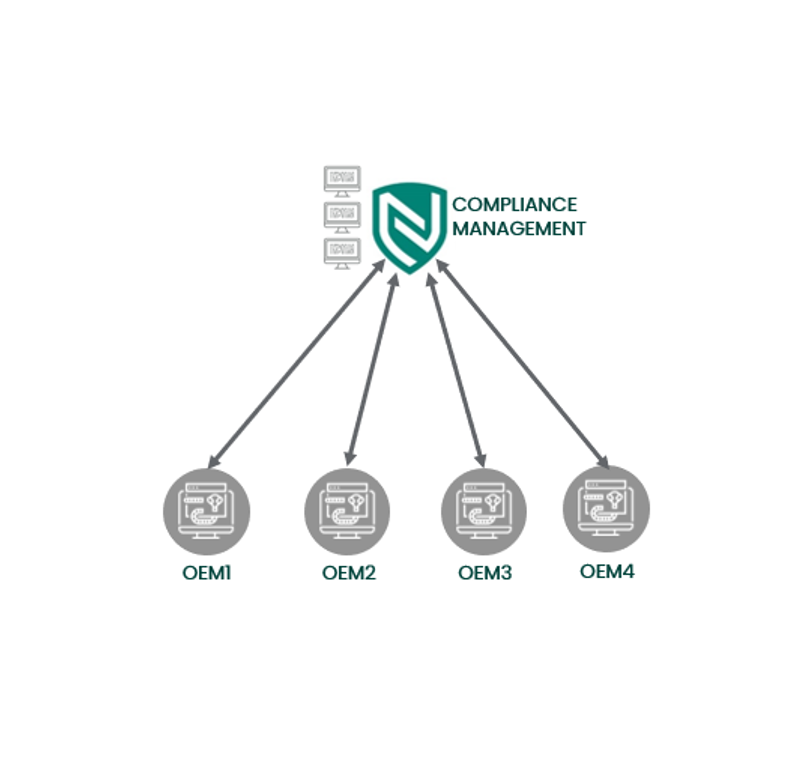
Policy Manager
- Establishes and maintains consistent compliance score
- 基于代理的和无代理的(关键供应商 - 不合稳定功能)
- Configuration assessment against 1000+ compliance policies, standards, and regulations
- Multi-Factor Authenticationencrypted remote access
- Secure gateway usingZero Trustsecure access solution
- Video replay technology formaximum isolationbetween plant operation assets and external remote access users
- 颗粒状访问控制机制和mediated remote file transfer
- 防止零日恶意软件utilizing advanced malware detection
- Simultaneous user access, ideal for a在家里工作environment















